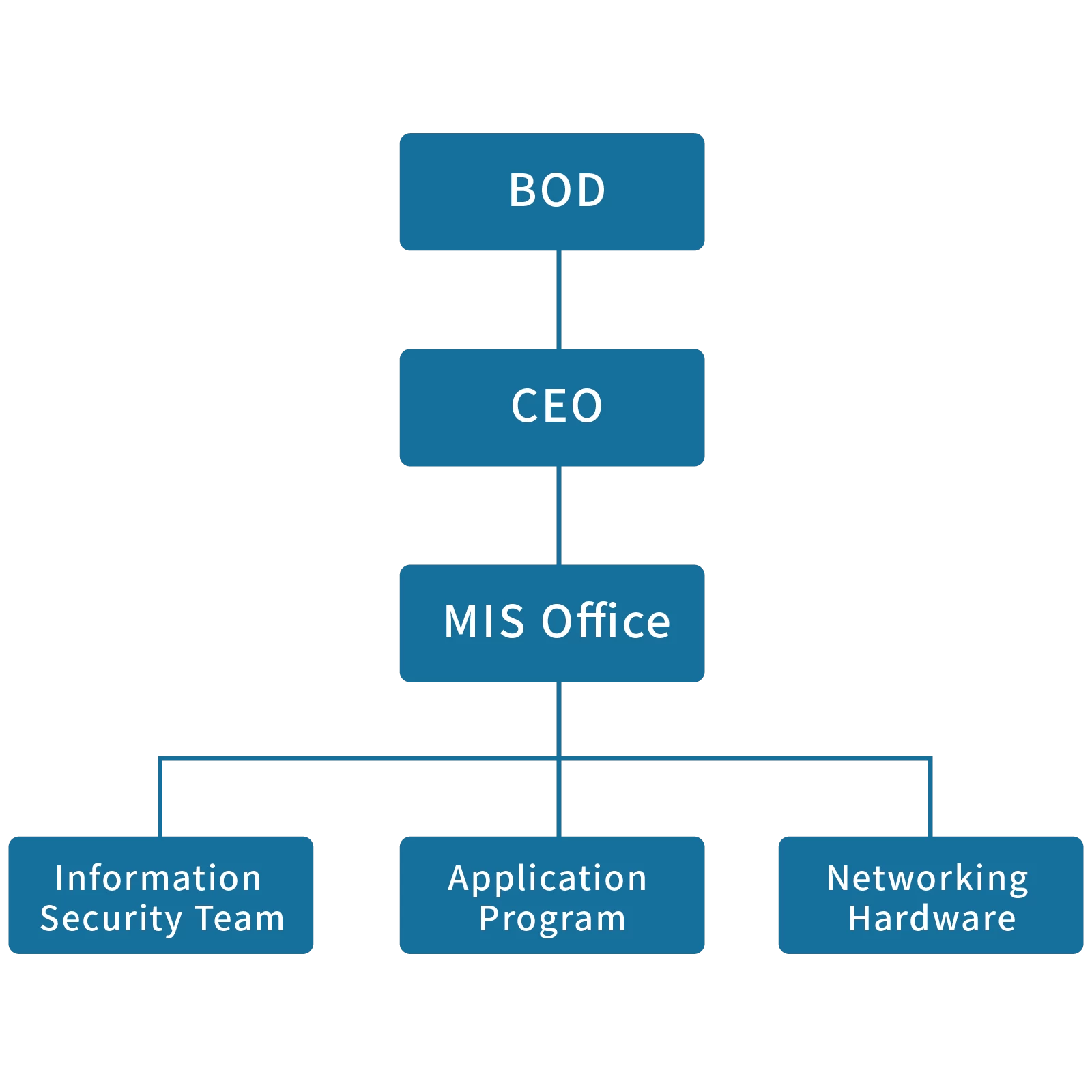
Cyber Security Management Structure
THC aims to enhance information security management by establishing a dedicated supervisor and personnel for information security. Under the Information Department, there is a subordinate information security team responsible for coordinating the formulation, implementation, risk management, and compliance auditing of information security policies. Information Security’s highest-level supervisor reports annually to the Board of Directors on the effectiveness of information security management, relevant security issues, and strategic directions. The internal announcement of the "THC International Information Security Policy" was made on March 21, 2023. The report on the effectiveness of information security execution in 2024 and the goals for 2025 was presented to the Board of Directors on May 9, 2025.
Cyber Security Policy
“To maintain the Company information security, conduct self-manage, and raise information security awareness”
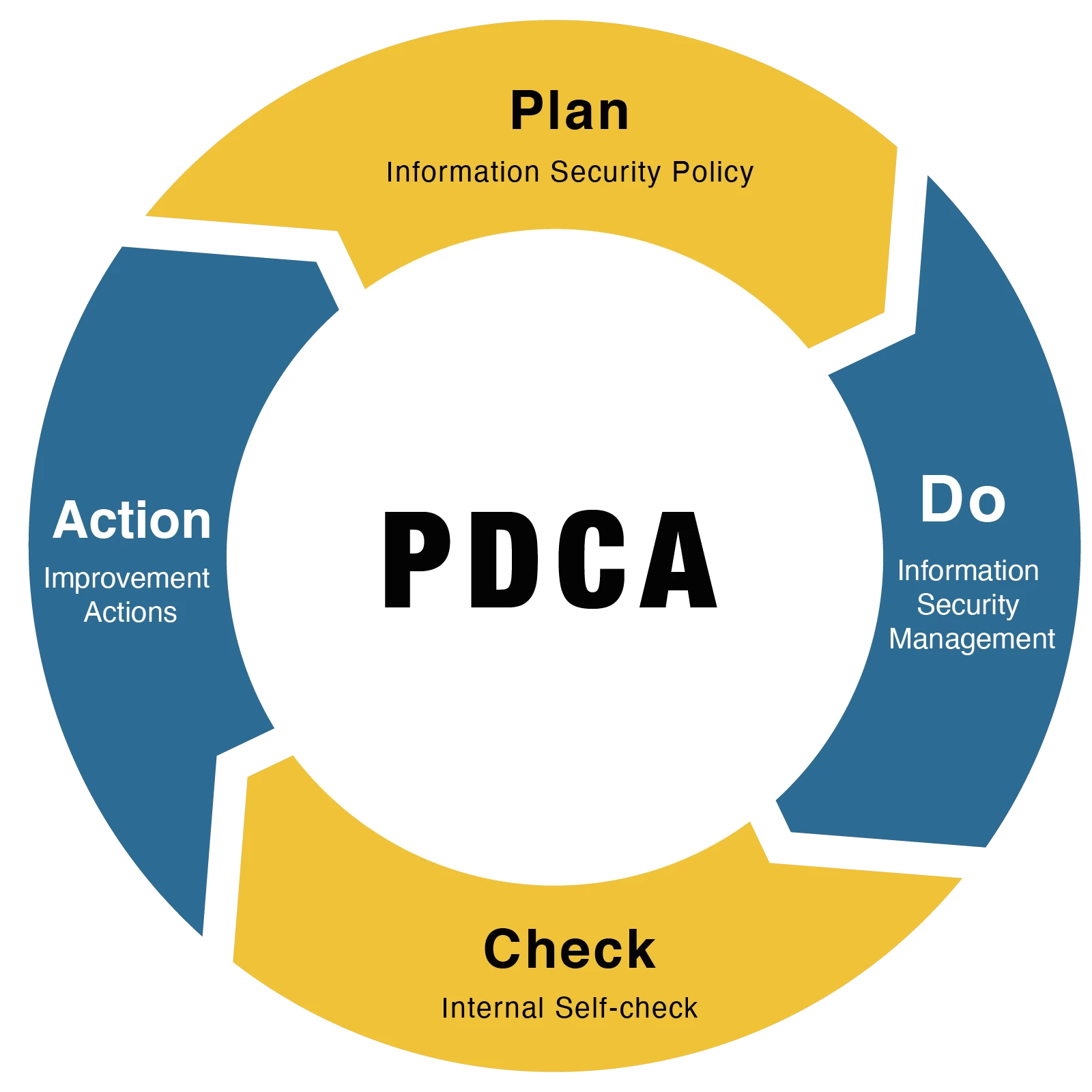
An Information Security Team let the Company's concept of information security take root through the “Information Protection Working Committee.” The Committee, which covers all organizations with Taiwan plants and overseas subsidiaries, convenes regular meetings to keep track of situations and utilizes the Plan-Do-Check-Act(PDCA) cycle to inspect the policy applicability and measures such as information protection.
| Plan | Refer to relevant information security systems, and formulate information policy and management measures. |
| Do | Multi-layer information security protection: and management (physical security, network security, device security, access management, and information security maintenance and operation.) |
| Check | Another row for testing the odd background. |
| Action | Review and improvement on information security measures, introduce the new information security protective tools, and training programs and promotion campaigns on information security. |
Concrete management programs
| Program | Explanation | Result |
|---|---|---|
| Social engineering drills and information security promotion | Conduct social engineering drills and information security promotion regularly. | In 2025, we conducted 2 times drills and 4 times promotion to cultivate employees' information security awareness. |
| Set multi-layer information security protection | Set up next-generation firewalls, intrusion detection and prevention systems, and email security filtering devices at gateway ends. Deploy important hosts with intrusion prevention antivirus and anti-intrusion systems. Deploy antivirus software on user computers. | Protect servers, networks, and computers. strengthens the depth of defense capabilities and reduces the chances of being attacked. |
| Vulnerability scanning and system update | Regular vulnerability scanning for hosts and networks, monthly system patch updates, and regular vulnerability scanning and remediation for publicly disclosed system vulnerabilities. | In 2025, we conducted 2 times vulnerability scans. We performed monthly patch updates for the Windows operating system to strengthen the patching of server and software vulnerabilities, reducing opportunities for hackers to exploit vulnerabilities. |
| Information security monitor | The personnel set up abnormal alerts for cyber security equipment and antivirus software and review security equipment and antivirus system logs daily. | The personnel promptly detect anomalies or attack behaviors and take immediate action to prevent the escalation of security issues. |
| Disaster recovery exercise | Perform regular differential restoration and backup data restoration tests for critical core systems. | In 2025, we conducted 2 times disaster recovery exercises to confirm the effectiveness of backup data. |
Investments in resources for cyber security management
In 2025, the corporate information security measures implementation results:
a. The core system to conduct disaster recovery drills: 2 times
b. Conducted email social engineering drills: 2 times
c. Information security promotion: 4 times
d. Vulnerability scanning and remediation for hosts and networks: 2 times
e. There has been no major information security incident occurred.
Although the Company has not purchased the cyber insurance, the performance of the Information Security Team and the implementation of the Information Security Policy can also create a secure IT environment to ensure the information security of the Company's various services.